Avoid The Social Media Binary
Many organizations today get caught up in what I call the “social media binary,” where there are only two options to social media control: 1) Allow unrestricted access to social networks, and potentially expose the company to myriad security, regulatory, reputational, and other risks, or 2) set and enforce policy that completely forbids the use of social media while at work, and forgo potentially lucrative business opportunities for the firm.
Neither option sounds appealing, but security and risk management professionals usually opt for the latter of the two. The business opportunity isn’t always apparent, but the risks are: malware, spearphishing, productivity loss, brand and reputational damage, legal and regulatory fines… the list goes on. This argument even seems to be supported by recent data estimating the annual productivity loss for your company may be as great as $4,452.00, per employee. This coupled with recent Twitter account hacks of Burger King and Jeep, and security breaches of the three main social networks all in the past year – Twitter, LinkedIn, and Facebook – means social media isn’t something to take lightly.
Before I convince you that the second option is the right approach, let me reiterate this point: It’s not. In fact, in a previous blog post of mine, I argue that you need to find a way to make social media work.
Not only is the above productivity loss data extremely misleading (I’ll spare you the long academic paper I could write on causation vs correlation or defining productivity to refute each point of the infographic), but there are a number of reasons why social media is a good idea: it can deepen customer relationships, improve worker efficiency, and even augment recruiting and retention efforts for your firm. Your ambitious, career-driven employees are the ones that will use social media for valuable business reasons (see the figure below). You must empower them with the tools they need.
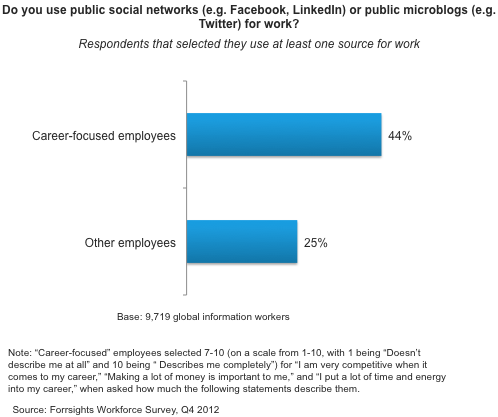
The point is, don’t settle for either option in the social media binary; consider the full social media control spectrum. Enable restricted access to social media, and apply technical social engagement controls, sound policies, and effective monitoring and oversight to ensure you manage social media risks effectively.
There are a host of available options for you to consider, but it requires strategic planning and more thought and effort than you may have considered in the past. During my track session at our Forrester Security Forum in Washington, DC (May 5-6), I will discuss how to avoid the social media binary, detailing the many technical options you have available to you, including social control systems, social engagement control platforms, and social listening platforms; I will highlight best practices and great case study examples to demonstrate how leading organizations are tackling social media issues. I hope you’ll join me.
Best regards,
Follow the Forrester Forum discussion by using the hashtag: #FORRForum