Mobile Security Technologies 2015
Today, I'm officially kicking off the 2015 version of the Mobile Security Technology Radar and I need your help!
Mobile security is one of the fastest changing, most dynamic markets that I have ever seen in my life (and I've been around the block a few times). Just when enterprises think they have it all figured out, a new shiny blinking toy is released that promises to secure mobility better than ever before. I began formally tracking the mobile security space for Forrester in the summer of 2013. One of my early reports was the 2013 Mobile Security Technology Radar which I slightly updated in the winter of 2014. Both enterprises and vendors alike responded very positively to these reports, citing the valuable insights that allowed them to predict the movements of a market that changes faster than Katy Perry at the super bowl halftime show.
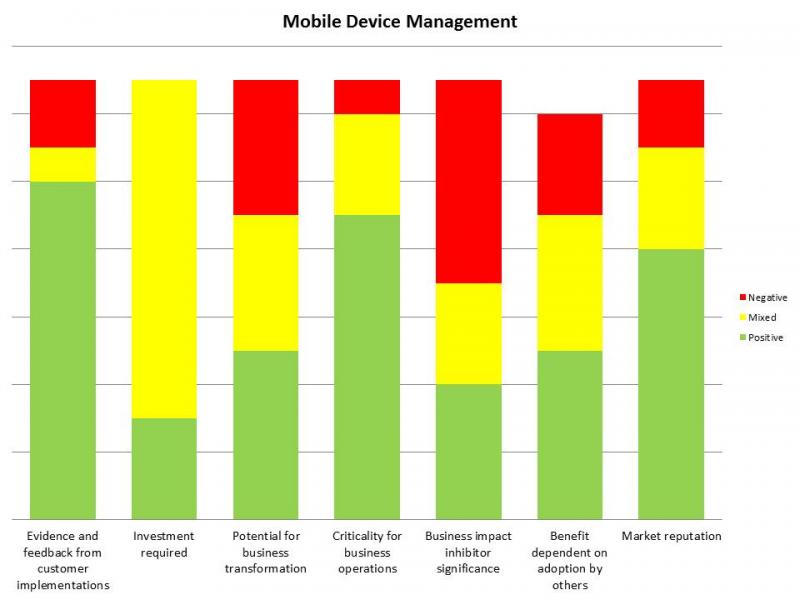
What isn't always evident in the reports that we write at Forrester is the depth and details in the research we do. For example, the graphic below represents quantified survey results of industry experts, vendors, and customers of mobile device management technologies that offers insite into the market sentiment on MDM solutions in 2013. MDM was a pretty hot technology in the summer of 2013 and the lack of red market sentiment helped us predict that this technology would thrive in the near future (see graphic below). Things really get interesting when we have year over year trending data to help us gain additional insite into the future market movements.
In the past we have included the following 15 mobile security technologies in the research project:
- Application Wrapping
- Data Wrapping
- Mobile DLP
- Mobile Application Reputation Services
- Mobile Static Code Analysis
- Secure Mobile Content Sharing
- Mobile Antimalware
- Containerization
- Mobile End Point Security
- Mobile Device Management
- Mobile Device Reputation
- Mobile Virtualization
- Secure Mobile Network Gateway
- Mobile Authentication
I'm asking for your thoughts, opinions, complaints, and suggestions going into this years 2015 report. These 15 technologies were the most important mobile security technologies two years ago. Some of them are no longer valid or may have merged into unified / shared offerings.
Please take a moment and email me (tshields@forrester.com) if you have any changes, additions, or deletions from this mobile security technology list that you feel we should include in this year's TechRadar report. I look forward to incorporating your thoughts into the 2015 version of this report.