Introducing Forrester’s Targeted-Attack Hierarchy Of Needs
We recently published part 1 of a new series designed to help organizations build resiliency against targeted attacks. In the spirit of Maslow, we designed our Targeted-Attack Hierarchy Of Needs. One factor that significantly drove the tone and direction of this research was Forrester client inquiries and consulting. Many organizations were looking for a malware sandbox to check off their targeted attack/advanced persistent threat/advanced threat protection/insert buzzword needs. Malware analysis has a role in enterprise defense, but focusing exclusively on it is a myopic approach to addressing the problem.
Part 1 of the research is designed to help organizations broaden their perspective and lay the foundation for a resilient security program. Part 2 (currently writing at a non George R.R. Martin pace) will move beyond the basics and address strategies for detecting and responding to advanced adversaries. Here is a preview of the research and the six needs we identified:
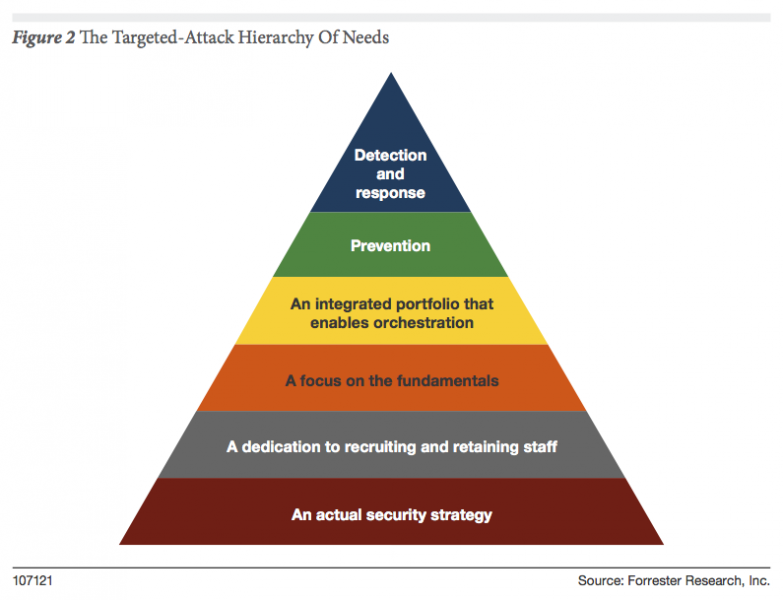
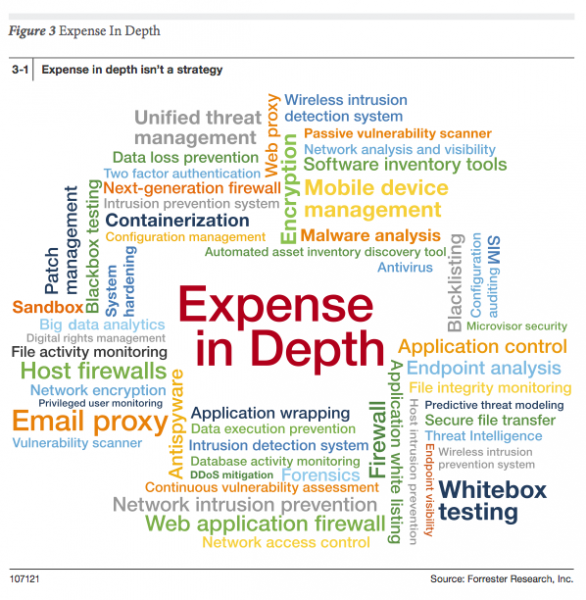
- Need No. 1: An Actual Security Strategy. Many organizations are running a race and they have no idea where the finish line is. If you don’t have a sound security strategy, you might fail at responding to commodity threats, and you will certainly fail at responding to sophisticated attacks. Before we jump to buying "advanced" security solutions and services, we must first understand the data and architecture of what we’re trying to protect. (This is fused with external data that incorporates attacker capabilities and motivations; more on that to come later.) The belief in silver bullets and “Expense in Depth” are two of the most common enterprise strategies I encounter. For more details on Expense in Depth, check out Expense In Depth And The Trouble With The Tribbles.
- Need No. 2: A Dedication To Recruiting And Retaining Staff. Technology is not a substitute for people; you can only maximize it when you have staffed your team appropriately with skilled and trained resources. You are going to have to come up with creative ways to find, develop, and retain talent. The most talented people in your environment shouldn’t be the adversaries. One example that I mention in the research is doubling down on higher education institutions. There is a race among public and private institutions to develop top-notch cybersecurity programs. Many of these programs don’t produce real world ready graduates. Get on the steering committee/board of these programs, drive the curriculum, and help the programs differentiate from the seemingly limitless competition.
- Need No. 3: A Focus On The Fundamentals. One of my favorite comments from the Verizon DBIR reports is “Would you fire a guided missile at an unlocked screen door?” Adversaries use only the minimal amount of effort required to achieve their mission. If you have a flat network architecture that enables your adversary to pivot across your environment with ease, you’re doing it wrong. Instead of investing in silver bullets, it might make sense to make sure you have focused on the fundamentals first. Some examples of fundamental missteps organization make:
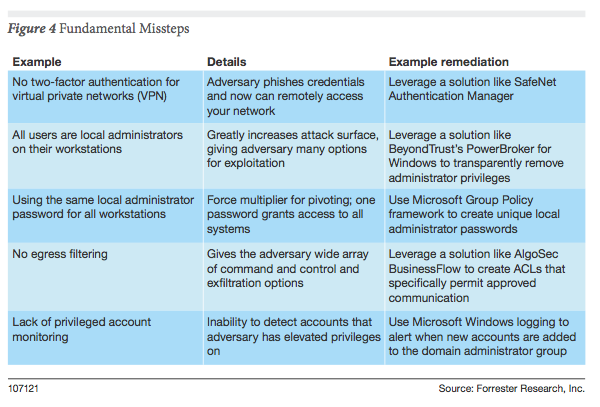
-
Need No. 4: An Integrated Portfolio That Enables Orchestration. How many manual processes does your organization have? If your organization is like any I’ve worked in, the number is countless. It’s very trendy to talk about creating friction for the adversary: increase their costs for targeting our environment to make their jobs more difficult. This is all well and good, but often this conversation doesn’t address the internal friction we create for ourselves. Lack of staff, inadequate training, and immature process and oversight all contribute to internal friction. The report outlines several strategies for addressing this need. Pressuring the vendor community is one of them; most companies cannot afford to stand up software development capabilities in order orchestrate their defense.
-
Need No. 5: Prevention. “Prevention is dead, long live prevention!” One of the recent trends in information security is to claim that prevention is dead. Like Catelyn Stark, prevention isn’t dead. You should be particularly suspect of vendors that only deal in detection that make this claim. Investment will shift to detection, but prevention isn’t going away; the reports of prevention’s death have been greatly exaggerated. You think you are overwhelmed now; can you imagine your incident response without prevention? More on this in part 2 of the research.
-
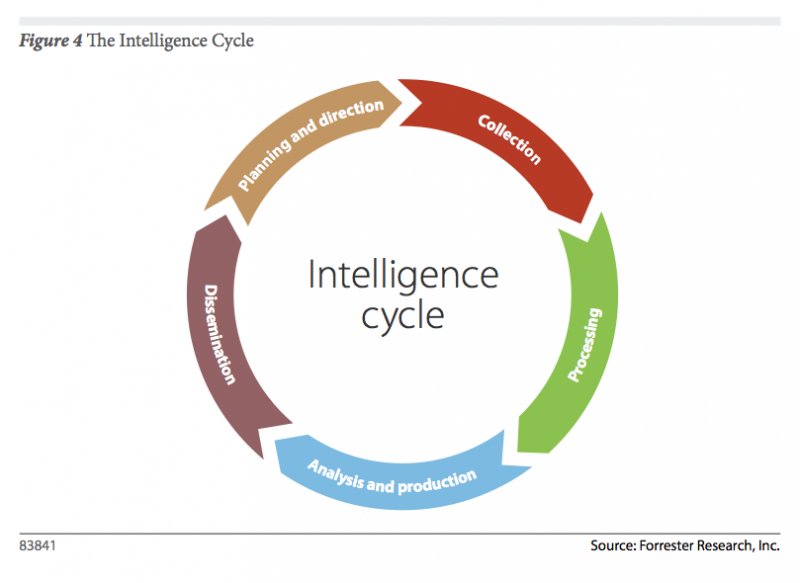
Need No. 6: Detection And Response. When dealing with adversaries that have both the motivation and capability to target your enterprise, timely detection and response will be the cornerstone of your strategy. In this section of the research I will discuss the role of Automated Malware Analysis, Network Analysis and Visibility, Endpoint Analysis and Control and Security Analytics in detection and response. The reality is that there isn’t one technology that serves as your breach detection system. Your enterprise, your staff, your process and your technology portfolio make up your breach detection platform. In many cases these will be complemented with third-party services. I will also discuss preparation of the battlefield, also known as your enterprise. You have home court advantage; you should take advantage of it. I will also go over the role of intelligence in defending against targeted attacks. Remember this graphic from Five Steps To Build An Effective Threat Intelligence Capability? We will revisit it.
If you aren’t a Forrester client and would like a copy of both reports (part 2 when it publishes), we are looking to conduct additional research interviews in this area. The interviews will be confidential; we won’t quote you and your organization won’t be mentioned. Please follow up with Katherine Williamson if you are interested. (kwilliamson at forrester dot com)