Take Security To The Zero Trust Edge
Forrester’s Take On The SASE Model
This is big, folks. This is really big. Bigger than GameStop. Even bigger than Heelys (the adult version saved in my Amazon wish list). This could be the biggest technological transformation since sliced bread, Dorito tacos, or public cloud.
A year ago, fellow Forrester analyst Andre Kindness and I set out to document a new model for security and networking that was gaining mindshare in the market. Well, just last week, we published the fruits of that research in a Forrester report titled “Introducing The Zero Trust Edge Model For Security And Network Services.” There’s a similar name going around in the market, “Secure Access Services Edge” (SASE — pronounced like it rhymes with “gassy”) to describe the same model, but we put the emphasis on the Zero Trust part (more on that in a minute).
I am an advocate for this model for several reasons. But the primary one is this: The internet was designed without security in mind. We’ve allowed it to become a toxic, malicious hive of scum and villainy. And we, as technologists, just expect every organization in the world to simply attach themselves directly to it and hope it all works out for them? For 25 years, we’ve just been putting Band-Aids on top of Band-Aids, hoping to stop the cybersecurity bleeding, but the carnage gets worse every year.
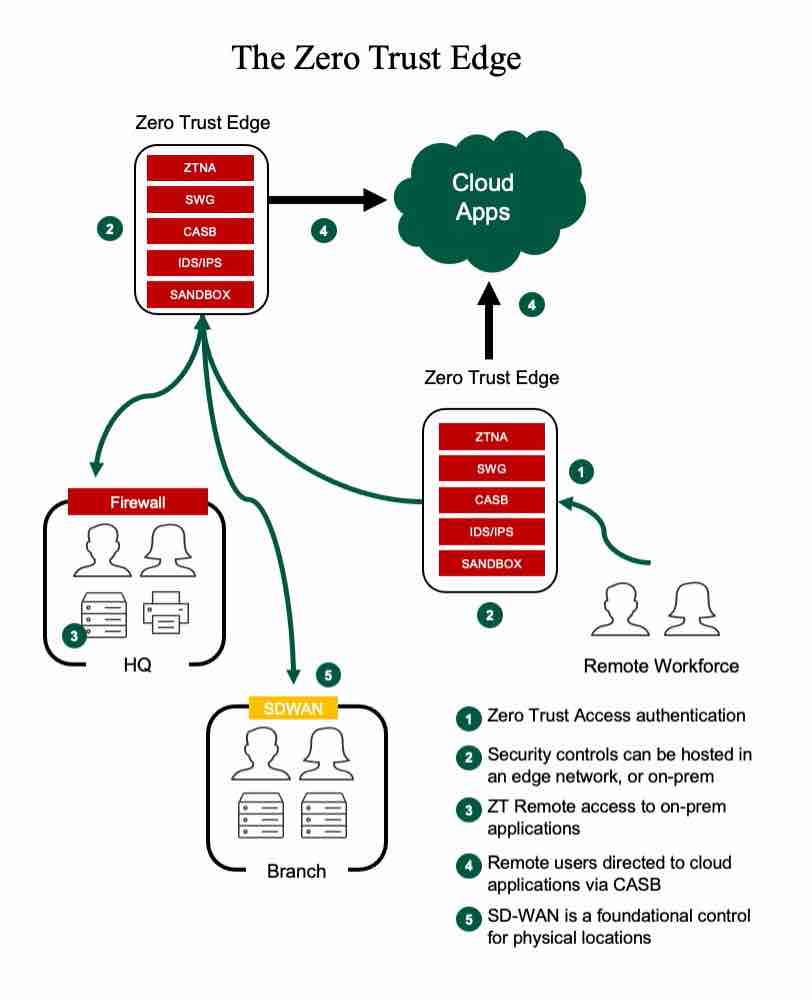
The Zero Trust Edge (ZTE) model is a safer on-ramp to the internet for organizations’ physical locations and remote workers. A ZTE network is a virtual network that spans the internet and is directly accessible from every major city in the world. It uses Zero Trust Network Access (ZTNA) to authenticate and authorize users as they connect to it and through it. If those users are accessing corporate services like an on-prem application or Office 365, they may rarely even “touch” the internet (except to be safely tunneled through it), and they’ll certainly be kept away from the bad parts of town.
Interest in this model over the past year has been intense. Well over half of the Forrester client inquiries I take are about this model. While many of the questions are very basic, like, “What’s this SASE thang I keep hearin’ ‘bout?” some of them are on target, such as, “David, should we be considering this model when we’re upgrading our firewalls?”
Tactics Vs. Strategy
The majority of enterprises I talk with are looking at this model to tactically solve a specific problem: securing the remote workforce. These organizations realize that acquiring more VPN licenses during the COVID-19 lockdown was just a stopgap measure to keep people working. Now, they’re looking for a ZTNA solution.
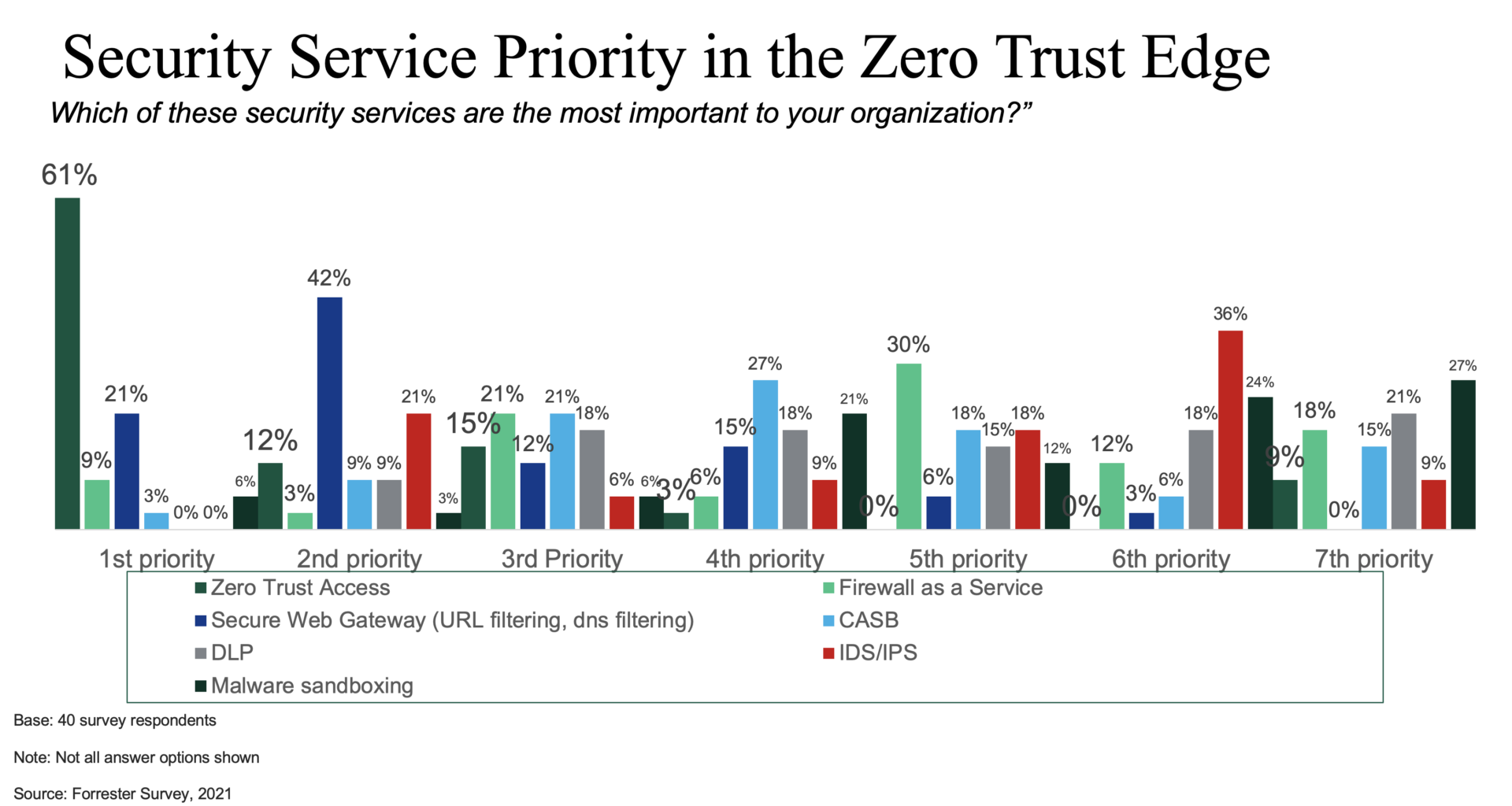
All ZTE vendors have ZTNA because it’s the primary security service of their stack. Once enterprises start talking with vendors like Zscaler, Akamai, or Netskope, they realize there are more security services they can consume as a service, and now they’re talking themselves into ZTE strategy.
In the future, after other technologies like SWG, CASB, and DLP are integrated into the stack, organizations will look to put all their network traffic through these ZTE networks. And that’s where the security and network teams will have to work together, because legacy on-prem networks are hideous heterogenous, and the migration of giant datacenters or 12-story hospitals using software-defined WAN (SD-WAN) as a transport into the ZTE networks will be a challenge. No one I’ve talked to has done it and honestly, these are still early days for the model.
So, we’ll solve the tactical problem (remote workforce) first with ZTNA. We’ll move on to the larger security challenges next. And finally, we’ll address the network. In the end, remote users, retail branches, remote offices, factories, and data centers will be connected to ZTE networks that will use Zero Trust approaches and technologies to authenticate, sanitize, and monitor connections through the network and into the internet and public clouds.
Questions Addressed By Our Research
Other questions we’ve researched and answered in our research include:
- Is this a multivendor or single-vendor game?
- What is the role of managed security services providers (MSSPs) in this model?
- What are the roadblocks on the way to ZTE nirvana?
- Do these solutions always require an endpoint agent?
- Why is network involved in this conversation?
- Can we replace our perimeter firewalls with SD-WAN?
Whew! Believe it or not, I typed all of that in 10 minutes. I’ve said all these things a hundred times on the phone, and I’m passionate about this new model. If you’re a Forrester client, read our report, “Introducing The Zero Trust Edge Model For Security And Network Services” and set up an inquiry with myself, Andre Kindness, or both of us.
