The Top Five Lies Security Vendors Tell About The SIEM
I’ve only been at Forrester for six months, and I’m already sick of hearing the phrase, “If you tried this query in the SIEM, it would take weeks!” and “Security teams hate their SIEM!”
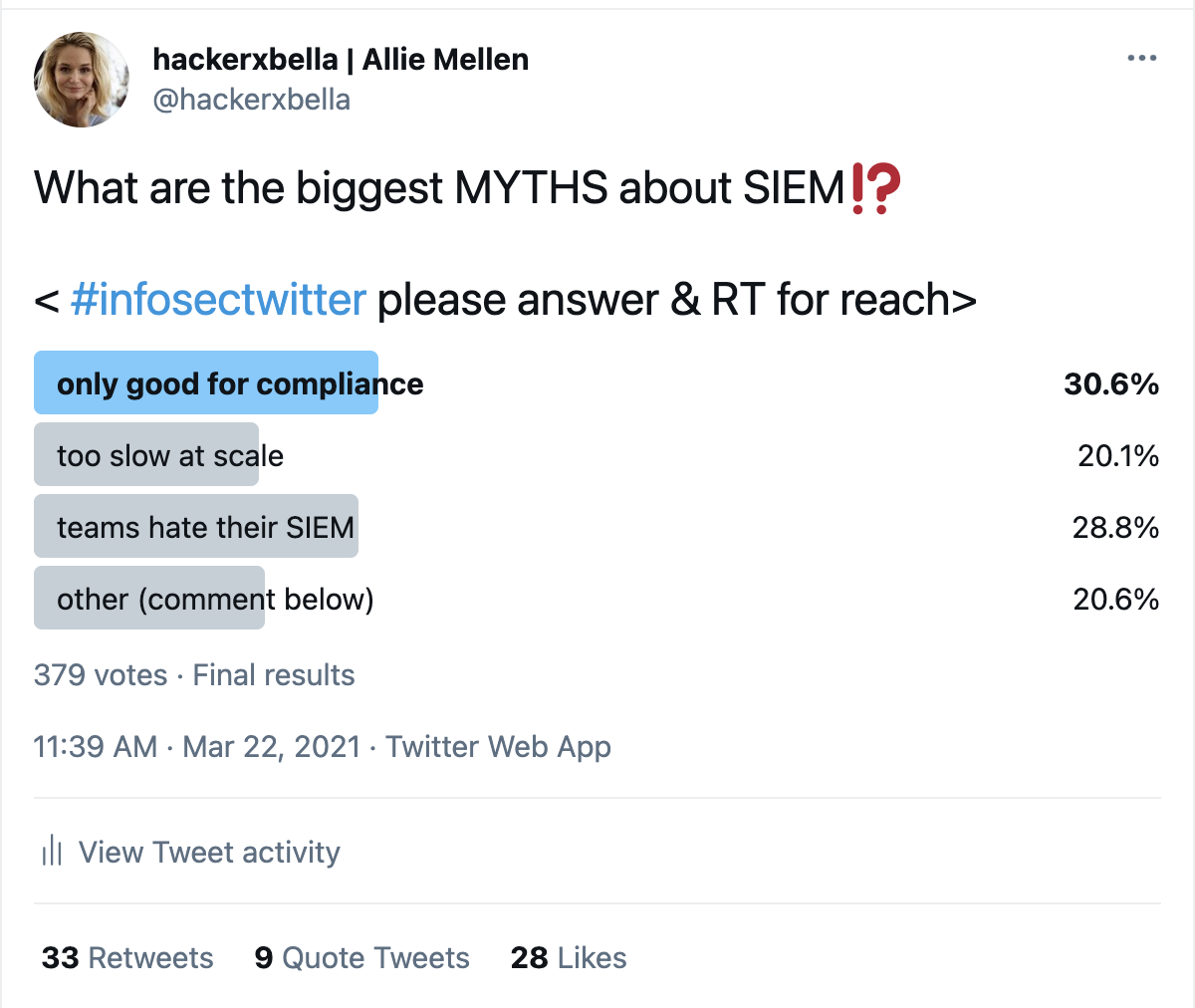
SIEMs (security information and event management systems) — especially those that have evolved into security analytics platforms — are not what they were 10 to 20 years ago. To figure out if this was widely known or only a luxury afforded to an analyst, I ran a survey to ask #InfoSecTwitter what people thought the biggest myths about SIEMs are, and the opinions were … strong.
(A screenshot of my Twitter poll on the biggest myths about SIEM)
Now, I received a lot of responses that hone in on the myths SIEM vendors tell you about their products (often in marketing and sales messages). And to be honest, many of them (including a comment by Katie Nickels) are accurate.
SIEMs do take work. They also require strategic planning and, much to the chagrin of everyone who believed the vendor hype, fail to provide the “single pane of glass” promised so long ago.
These, however, are not the myths I am going to debunk today, as that would be akin to pushing water uphill with my bare hands. It’s not possible, particularly with these white-collar, uncalloused mitts.
With all that said, there are some aspects of the SIEM that have improved significantly over the past 20 years, despite a barrage of security marketing suggesting otherwise. Below, I take a page from the book of my old combinatorics class and provide a disproof by counterexample (in some cases x2) for each of these five myths.
I chose to omit links to actual vendor marketing messages that push these myths; rest assured, however, that you can find every single one with a simple Google search.
Lie Number One: SIEMs Are Only Good For Compliance
Security analytics platforms are pushing hard for differentiation in the detection and response space, with solutions like Exabeam and IBM Security making it a point of contrast in the latest Forrester Wave™ evaluation on security analytics platforms. In addition, even as recently as 2019, solutions such as Microsoft Sentinel were roaring into the space, purpose-built for security use cases.
Lie Number Two: SIEMs Don’t Scale
Querying at scale is a long-recognized challenge of legacy SIEM solutions; when you intentionally create a big data problem, you must also find a way to solve it. What many security teams find is they often struggle with scaling the SIEM because of the way they approach log collection — instead of thinking about it strategically, it becomes all or nothing.
There are cases, however, in which enterprises, such as large players in the financial services vertical, just need to collect ridiculously vast amounts of data. There are incredibly fast solutions on the market and significant innovation happening in this space today to address this with solutions like Devo and Chronicle.
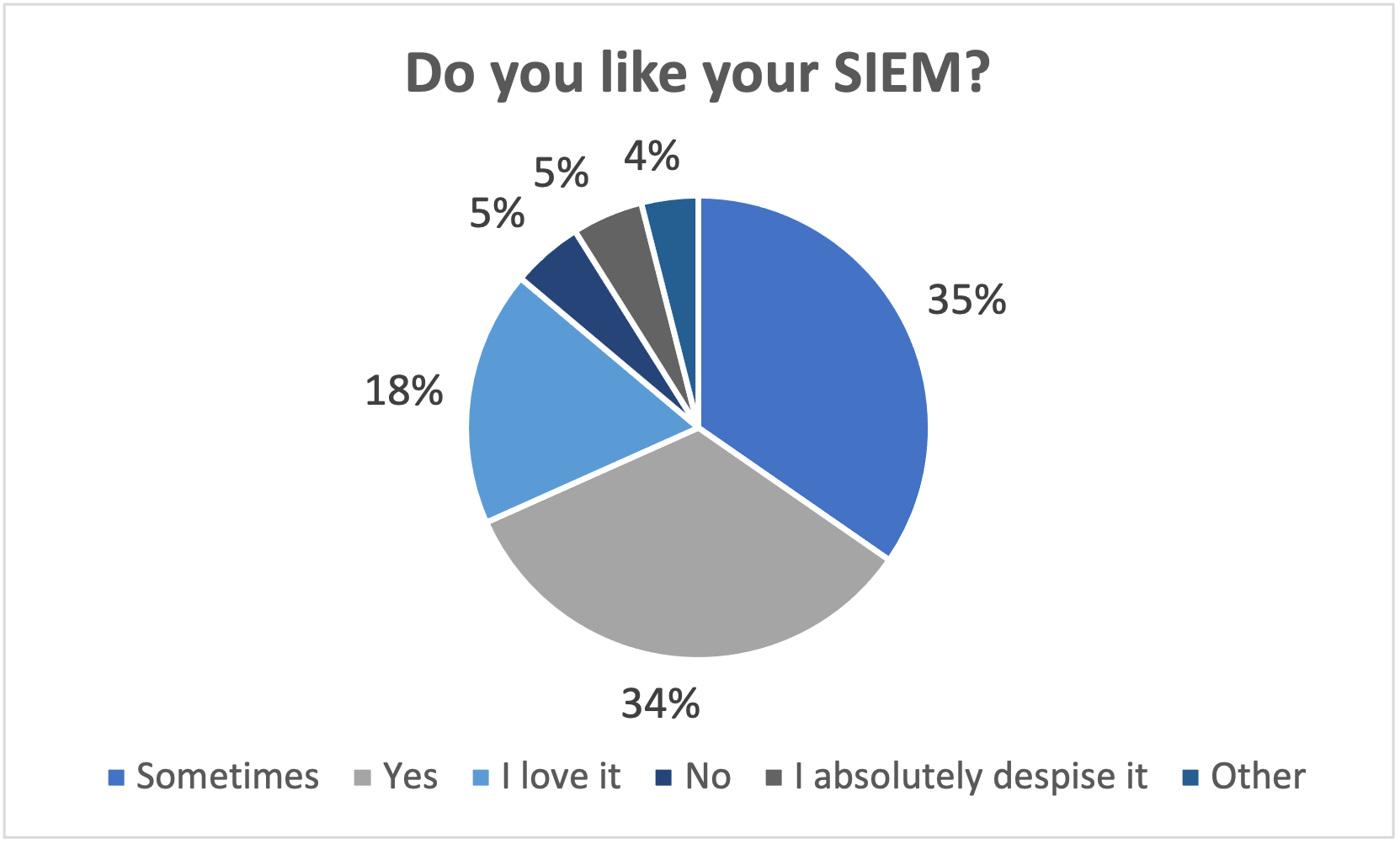
Lie Number Three: Security Teams Hate Their SIEM
As my research director Joseph Blankenship would say, if you’ve ever attended one of Splunk’s .conf events, you know there are practitioners who love their SIEM. And it’s not just anecdotal data driving this notion — according to a recent poll we ran, over 50% of respondents like or love their SIEM.
Lie Number Four: SIEMs Don’t Do Orchestration Of Response
This was kind of true a few years ago but mostly not true at this point. Ultimately, security orchestration, automation, and response (SOAR) technology has been or is being absorbed by larger SIEM players, to the point where many security analytics platforms incorporate automation and orchestration. This is quantified in the latest Forrester Wave evaluation on security analytics platforms and exemplified in solutions like FireEye Helix, Microsoft Sentinel, and IBM QRadar.
Lie Number Five: SIEM Is Dead
This one is just a tad ridiculous and overblown. SIEMs remain a core part of the security operations technology stack for most mid-to-large enterprises, and according to Forrester’s “The State Of Network Security, 2020 To 2021” report, security teams that experience a breach are expanding their security monitoring, not stifling it. Ultimately, the SIEM remains the operating system of the security operations center, and it isn’t going away, despite challengers like extended detection and response (XDR) rising up as competition.
In Conclusion
Are there challenges with security analytics platforms/SIEMs? Absolutely. This is in no way a tacit endorsement or defense of the shortcomings of SIEM technology. If you came to this blog looking for how to bridge the gaps SIEM has been unable to fill, check out my webinar on XDR’s collision course with SIEM and SOAR.
This post is to say, however, that the way we thought about SIEM 10 years ago is not representative of the multifaceted tool that security teams use today. Security analytics platforms have a fighting chance of maintaining their stronghold over this space if they focus on innovation in detection, exceptional user experience, and automation for investigation and response.