Authors:
Merritt Maxim, Jeff Pollard, Jess Burn, Sandy Carielli, Janet Worthington, Allie Mellen, and Brian Wrozek
Contributors:
Joseph Blankenship, Stephanie Balaouras, Heath Mullins, Andras Cser, Carlos Rivera, David Holmes, Heidi Shey, Hailey DiCicco, and Peggy Dostie
A Tough Economy Demands Spending Vigilance Without Sacrificing Trust
The continued onslaught of breaches, ransomware, legislation, and third-party requirements has forced executives outside of security to recognize the importance of comprehensive cybersecurity controls. As a result, security, privacy, and other risk leaders now find themselves in demand from the board and throughout the enterprise. However, this raised profile has created new challenges, including a growing list of cybersecurity technologies and vendors necessary to provide protection; continued staffing shortages that compromise the ability to roll out new technologies (and support existing ones); and extensive rework and customization to integrate specific technologies to meet business requirements.
S&R leaders must manage these challenges at a time when instilling and maintaining trust with customers, employees, and partners is a business imperative and when geopolitical events and technology disruption continue to fuel a highly sophisticated and evolving threat landscape. And while business leaders are far less likely to target security investments during economic downturns, it would be unwise for S&R leaders not to join their IT counterparts to assess their spending across the board to ensure maximum value.
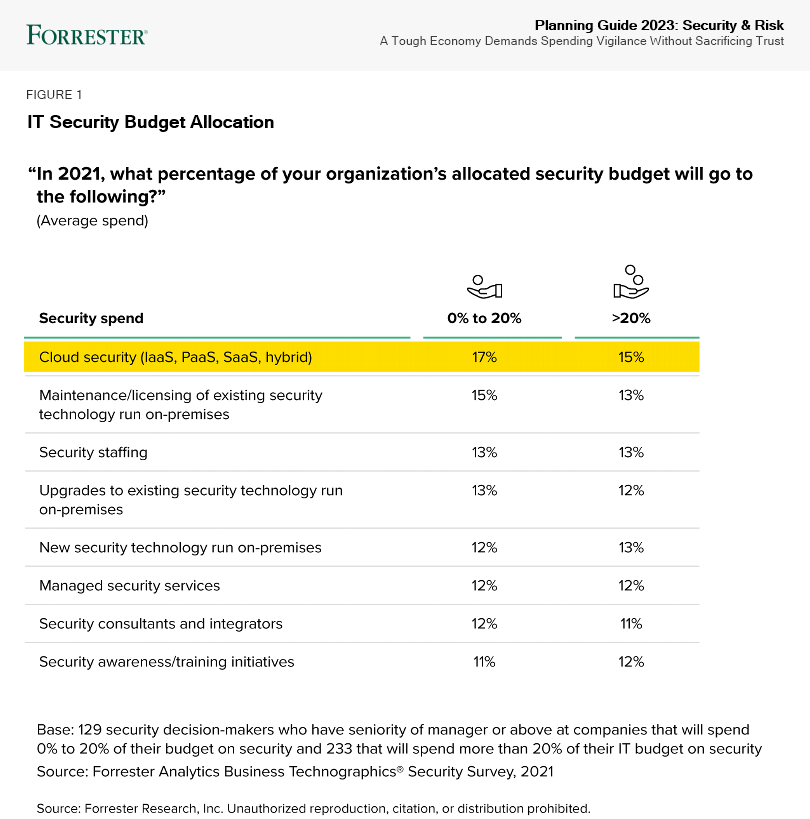
Benchmark Current Spending
Forrester’s Security Survey, 2021 provides an essential overview of budgetary allocation for security (see Figure 1). Our data provides a comparison of security budgets by two brackets: those that spend 0% to 20% of the IT budget on security and those that spend more than 20%. Compare your spending against our data to uncover where you may already be over- or underspending:
- Cloud security spending continues to ratchet up. Firms are reaching a new scale of cloud usage — particularly in the US. Forrester’s 2021 data shows that, on average, infrastructure decision-makers at US enterprises have migrated 45% of their total application portfolio to a public cloud. They anticipate 58% will have moved in the next two years. Security teams are spending a notable amount on cloud security, but given the percentage of workloads migrating to the cloud, they need to spend far more.
- On-premises technology spending remains significant despite the shift to cloud. When we combine the expenditures for maintenance and licensing, upgrades, and new investment, on-premises technology spending is by far the largest expenditure in the security budget — 41% for those in the lower-budget bracket and 38% for those in the higher-budget bracket. Since many applications and workloads have transitioned to the cloud, this suggests potential misallocation of security budget. CISOs should closely scrutinize on-premises spending to determine if it aligns with the cloud and modernization strategy of the overall IT organization.
- Expenditures on services nears a quarter of all spending. Due to the myriad individual security controls and the complexity of integrating them, security teams need external consultants and integrators to optimize their technology, assess their environment for weaknesses, and continuously evaluate their overall security posture and maturity. And whether it’s to reduce costs or address the skills gap, security teams turn to managed security services providers (MSSPs) for a variety of outsourced security needs. The shift to cloud won’t reduce services budgets anytime soon, not when organizations need help with modernization and migration. We expect traditional spending on MSSPs to shift to new offerings and new providers that offer better outcomes.
- Staffing and security awareness/training spend addresses skills gaps and culture. CISOs have struggled for years to recruit and retain security talent for a variety of reasons — many self-inflicted, such as uncompetitive pay, unrealistic expectations, and a failure to adapt how they recruit. And even before the worsening economic environment, CISOs found it difficult to justify their security awareness and training (SA&T) investment and understand the impact of initiatives beyond how many employees were trained: “Are user behaviors changing? Is our human risk lower?” It’s tempting to cut spending in these areas when the economic picture darkens, but it won’t save much compared with other expenditures, and it will exacerbate the skills shortage and sacrifice the ability to instill trust just when borderless, anywhere work organizations need it most.
Increase Or Defend Investment In Critical Apps And Cloud Security, Zero Trust Tech, And Ops
Cyberattacks and data breaches don’t pause with an economic slowdown. When prioritizing security investments, security leaders should continue to invest in security controls and solutions that protect the organization’s customer-facing and revenue-generating workloads, as well as any infrastructure critical to health and safety for those organizations in industries such as utilities, energy, and transportation. Next, security leaders should continue to defend any investments that support the organization’s modernization efforts with cloud and its evolution to Zero Trust. Finally, when the inevitable attacks and breaches occur, organizations need to be able to detect these incidents sooner and respond more quickly and effectively. Forrester recommends increasing or defending investment in these key cybersecurity functions:
- API security. API-first is the de facto modern development approach, and APIs help organizations create new business models and methods of engagement with customers and partners. However, security breaches due to unprotected APIs and API endpoints are common. No single type of tool fully addresses API security. Traditional security tools such as WAFs and bot management solutions are expanding to cover API attacks, and API management tools address security issues such as authentication and authorization. Meanwhile, API-specific security tools conduct scanning and discovery; some also add runtime protections and microgateways.
- Bot management solutions. Bot management solutions actively profile traffic to determine intent and perform protection techniques such as delaying, blocking, or misdirecting traffic from bad bots. With bad bots comprising 25.6% of total internet traffic in 2020, these solutions will be under pressure to operate under heftier scale and speed requirements. The market has consolidated, with WAF and content delivery network (CDN) companies acquiring bot management specialists or building bot management features into their offerings; at the same time, remaining bot management specialists and advertising verification and brand safety technologies also claim market share.
- ICS/OT threat intelligence. Organizations in the manufacturing, utilities, energy, and transportation industries use ICS threat intelligence capabilities to protect physical and digital assets, find indicators of compromise (IOCs), learn about emerging ICS threats, ensure safety, and prevent unplanned shutdowns. As threats increasingly target and affect industrial processes, CISOs will better manage risk to their firm’s core business with products designed for these environments.
- Cloud workload security (CWS), container security, and serverless security. To secure cloud deployments, security teams must use several specialized solutions. CWS technologies, which includes cloud workload protection and cloud security posture management, are crucial to secure the compute, storage, and network configurations of cloud workloads in IaaS and PaaS environments. Meanwhile, security pros contending with uncontrolled access to running containers and other container security challenges will have to stitch together a complete solution themselves, as the market is immature and many vendors, such as host OS providers, secure only part of the overall container ecosystem. Finally, as developers embrace serverless functions, security pros will need to investigate serverless security lest they end up repeating their experiences in container security.
- Multifactor authentication (MFA). The password is dying out, but it’s hard to completely eradicate: Although it’s snoopable, decryptable, fishable, and stuffable, it’s also simple, cheap, and easy to implement. As passwords become easier to undermine, security teams increasingly depend on MFA. These MFA solutions add a what-you-are (biometric), what-you-do (behavioral biometric), or what-you-have (token) factor to what-you-know (password or PIN code) single-factor authentication. MFA remains one of the simpler and higher-value security technologies that orgs can deploy to minimize the risks of password-based attacks and keep your cybersecurity strategy aligned around Zero Trust principles. Passwordless authentication technologies are also emerging, as the next evolution after MFA as passwordless technologies can completely eliminate the password and other replayable credentials from the authentication flow.
- Zero Trust network access (ZTNA). The convergence of networking and security capabilities continues to drive ZTNA adoption to fulfill the tenets of Zero Trust and Zero Trust Edge (ZTE) models. The recent explosion of remote workers created an absolute requirement for robust network access controls, as VPN solutions fell to the wayside due to antiquated methodologies for network connectivity. Combined with software-defined perimeters, ZTNA provides an agile and flexible solution for secure remote access, regardless of location. Resources residing on-prem, in the cloud, or as part of a hybrid architecture are accessible based on policy, allowing for fine-grained control of who or what can access a particular asset.
- Security analytics platforms. Rapidly evolving threats have overwhelmed legacy rules-based SIEM offerings and forced vendors to expand into security analytics (SA) platforms. SA platforms combine big data infrastructure, security user behavior analytics (SUBA), and security orchestration, automation, and response (SOAR) with traditional SIEM capabilities. SUBA offerings use behavioral analytics and are a principal technology for identifying insider threats. SOAR provides orchestrated processes and automation to give security pros better visibility, improved detection, and enhanced workflow.
- Crisis response simulations and purple team exercises. These activities test real-life scenarios for defenders, incident responders, and other stakeholders. Cybersecurity crisis simulations go beyond the technical tabletop exercises that security and IT conduct. They include the executive leadership team and board of directors. Often facilitated by an incident response services provider, outside counsel, or both, these exercises run executives through a breach or ransomware scenario. Purple team exercises are collaborative efforts between offensive security teams (who act as intruders) and defenders. Defenders can validate defenses, identify control gaps, find weaknesses, and learn how adversaries adapt moment to moment. Those without internal red teams can look at open cyber range providers for lab-like environments, or use tools such as Atomic Red Team and BloodHound for an organic do-it-yourself approach.
Reduce Or Avoid Investment In Standalone Controls Or Legacy, On-Premises Networking Tech
CISOs struggle with IT complexity, not only of the IT environment they must secure, but of the dozens of standalone security controls they have deployed. Business and its IT counterparts are modernizing with cloud and aggressively pursuing cloud-first strategies, but security investment in the specialized solutions for cloud workloads and cloud-native technologies hasn’t followed suit. In healthy or tough economic times, it’s always a good idea to decrease investment in standalone solutions and legacy, on-premises security controls. Forrester recommends decreasing or avoiding investment in these existing categories of spending:
- Standalone data loss prevention. Data loss prevention (DLP) technologies help organizations enforce data movement policies for sensitive data. DLP is often a feature capability in email security and cloud security gateways, cybersecurity suites, and platforms like O365, making it easier for organizations to acquire and enable DLP as a feature of a broader solution to address compliance needs.
- Standalone security user behavior analytics. SUBA solutions use behavioral analytics and machine learning to provide visibility across networks, devices, and applications. They are a principal technology for detecting insider threats. Since being introduced, many SUBA solutions have been assimilated or evolved into SA platforms. They are also being sold alongside DLP to provide additional user context. As a result, SUBA’s viability as a standalone technology is in doubt.
- Managed security services providers. MSSPs are third-party organizations that continuously and remotely manage and monitor security technologies for their customers. The four primary MSSP domains include, but are not limited to, perimeter and network security, application security, endpoint security, and identity and access management. MSSPs offer multitenant service delivery, automation, and one-to-many support models to maximize economies of scale. Over time, MSSPs devolved into alert factories sending templated emails about alerts to clients that failed to provide context or accelerate decision-making. As MSSPs wane, swap those investments to managed detection and response (MDR) or security operations center as a service (SOCaaS) providers.
- Indicators of compromise (IOC) feeds. Indicators of compromise feeds provide a list of capabilities that are used in malicious activity and attacks. Vendors are now building IOC feeds into other enterprise security controls such as enterprise firewalls, endpoint detection and response, and security analytics platforms so security pros can reduce or avoid spending money on duplicate IOC artifacts.
- Legacy, on-premises network security technologies. Security pros used to rely on standalone secure web gateways (SWGs) to enforce web-related security policies. Currently, large enterprises use SWGs to secure legacy infrastructure, or for use cases that require on-premises hardware. Similarly, they relied on standalone IPS to protect network perimeters. Now that applications are moving to, or already are in, the cloud, and users have shifted to a hybrid work model, security pros should move away from this antiquated solution set. Security leaders should also avoid investment in on-premises network access control (NAC), which is complex to deploy and often has very limited success, except for specific IoT/ICS/OT use cases. For all of these capabilities, CISOs should turn to more powerful and integrated solutions like NGFW and ZTNA combined with software-defined perimeters.
Experiment With Better Threat Insight, Detection, And Response, Plus Privacy Tech For AI
While there is nonstop innovation in cybersecurity, Forrester sees growing and promising value in these four categories. In the coming fiscal budget cycle, S&R pros should consider evaluating these technologies and funding proof of concepts — even in a downturn:
- Software supply chain security. Securing your software supply chain starts with understanding the underlying components that your organization builds, purchases, and uses. A software bill of material (SBOM) provides an ingredient list for including open source and commercial libraries. Request SBOMs from suppliers during the purchasing process. Tools such as Cybeats, Dependency-Track, and ION Channel can enrich SBOMs with supply chain intelligence. Your existing software asset management, configuration management database, or GRC systems might store or use the information from the SBOM analysis. Suppliers can use software composition analysis (SCA) tools to generate SBOMs to correlate known vulnerabilities, evaluate software licenses, and detect and block malicious components from entering the SDLC. For open source projects without an available SBOM, use an SBOM generation or SCA tool to create and analyze one for the project.
- Extended detection and response (XDR) and managed detection and response (MDR). XDR tools provide behavioral detections across security tooling to deliver high-efficacy alerts, additional context within alerts, and the ability to detect, investigate, and respond from a single platform. Most current XDR platforms prioritize endpoints for visibility, detection, and response and augment endpoint telemetry with other data sources such as NGFW, identity, and more, depending on the vendor. MDR service providers offer more mature detection and response outcomes than XDR products and can help augment security teams struggling to find or retain talent.
- Attack surface management (ASM) and breach and attack simulation (BAS). ASM solutions help organizations identify, attribute, and assess the exposures of newly discovered and known assets for risks like vulnerabilities and misconfigurations. Additionally, BAS has emerged to provide an attacker’s view of the enterprise with deeper insights into vulnerabilities, attack paths, and weak/failed controls. Both solutions assist security and IT ops teams in prioritizing remediation efforts based on the value of the asset and severity of the exposure. Organizations suffering from cloud sprawl and shadow IT should experiment with ASM and BAS for greater visibility and improved efficacy of remediation.
- Privacy-preserving technologies (PPTs). Privacy concerns are a major barrier to AI adoption. For AI-driven, advanced analytics use cases that hinge on data sharing across multiple parties, these concerns are even greater. PPTs include homomorphic encryption, multiparty computation, federated privacy, and others. It enables organizations to protect customers’ and employees’ personal data while processing it, such as when exploring personal data to build data models for AI or sharing sensitive personal data across the organization for analytics projects. PPTs promise to unleash the potential of high-performance AI models while satisfying privacy, ethics, and other regulatory requirements. PPTs promise to unleash the potential of high-performance AI models while satisfying privacy, ethics, and other regulatory requirements.
More From Forrester
Is your security plan robust enough to handle what’s coming in 2023? Watch this webinar and hear our analysts describe what security leaders should be considering for the year ahead.