Introducing A New Incident Response Metric: Mean Time Before CEO Apologizes (MTBCA)
For years cybersecurity professionals have struggled to adequately track their detection and response capabilities. We use Mean Time to Detection/Containment/Recovery. I wanted to introduce an additional way to track your ability to detect and respond to "sophisticated" adversaries: Mean Time Before CEO Apologizes (MTBCA). Tripwire’s Tim Erlin had another amusing metric: Mean Time To Free Credit Monitoring (MTTFCM).
Here are some examples (there are countless others) that illustrate the pain associated with MTBCA:
1) CareFirst breach announced 20 May 2015

2) Premera breach announced 17 March 2015

Your CEO doesn't want to have to deliver a somber apology to your customers, just like you don't want to have to inform senior management that a "sophisticated attack" was used to compromise your environment. Some of these attacks may have very well been sophisticated but I'm always skeptical. In many cases I think sophisticated is used to deflect responsibility. For more on that check out, "The Millennium Falcon And Breach Responsibility."
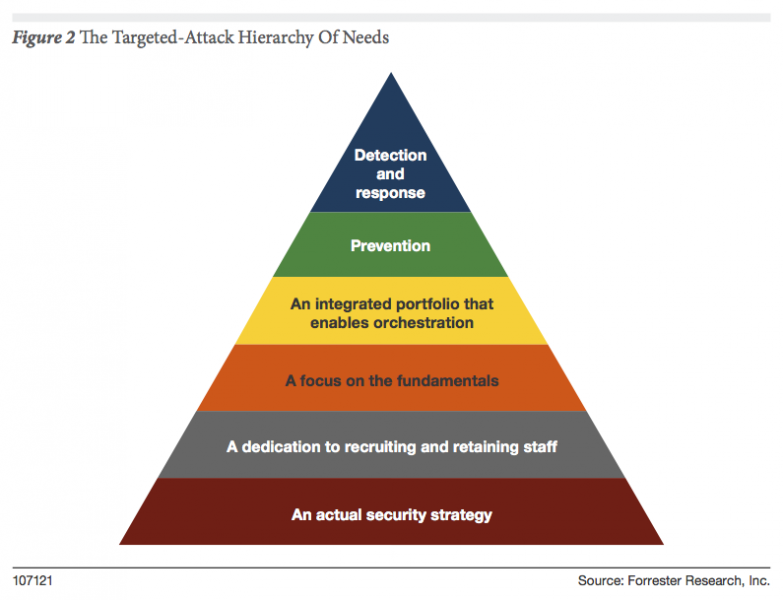
What are some ways that you can reduce your MTBCA? I'm glad you asked. Let me start with the RSA Conference and all of the "silver bullets" designed to save of from the enemies that are inside the wire. Threat intelligence, threat intelligence sharing, breach detection systems, machine learning, predictive analytics could help us out, but it is imperative to remember that your actual detection and response capabilities includes your staff, enabled by process and supported by technology. Last year I wrote the "Targeted-Attack Hierarchy Of Needs" to address this. Following the principals of the hierarchy can help you ensure your organization has as strategy that will reduce or eliminate your MTBCA.